Lynis will perform a few checks and then stops to give you some time to read the results. Edit root's cron file e. Very helpful and useful article. This program is required to run this script and comes with the package. Do you already have an account? It will now inform you about unusual system events, security violations, system attacks, etc. Just a little info:
| Uploader: | Gardaramar |
| Date Added: | 11 February 2012 |
| File Size: | 33.28 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 28276 |
| Price: | Free* [*Free Regsitration Required] |
Three Tools to Scan a Linux Server for Viruses, Malware and Rootkits
See how your visitors are really using your website. Now we have to create a cron job in order to run logcheck periodically. Good to know Thank you: Replace the path to chkrootkit with the path you received from the above command and exchange the email address with your actual address.
This feature is only available to subscribers. We will run portsentry in advanced stealth mode as it is the most powerful way to detect portscans: Lynis formerly rkhunter is a security auditing tool for Linux and BSD based systems. Scanning progress is shown.
Get your subscription here. Yes, my password is: Un-comment these if you are really anal: No, create an account now. This document comes without warranty of any kind!
SlackBuilds Repository
ISPProtect requires clamav chkrootkit.tar.vz be installedapt-get install clamavI've also found rkhunter useful. This way you can assure that the libs things like bash, lsof, ps and others link into are not hacked. The rest of portsentry. I am wondering if you would be able to point me in the direction of existing joint ventures working on puting inexpensive hardware and opensource between everybody and the internet.
locally checks for signs of a rootkit
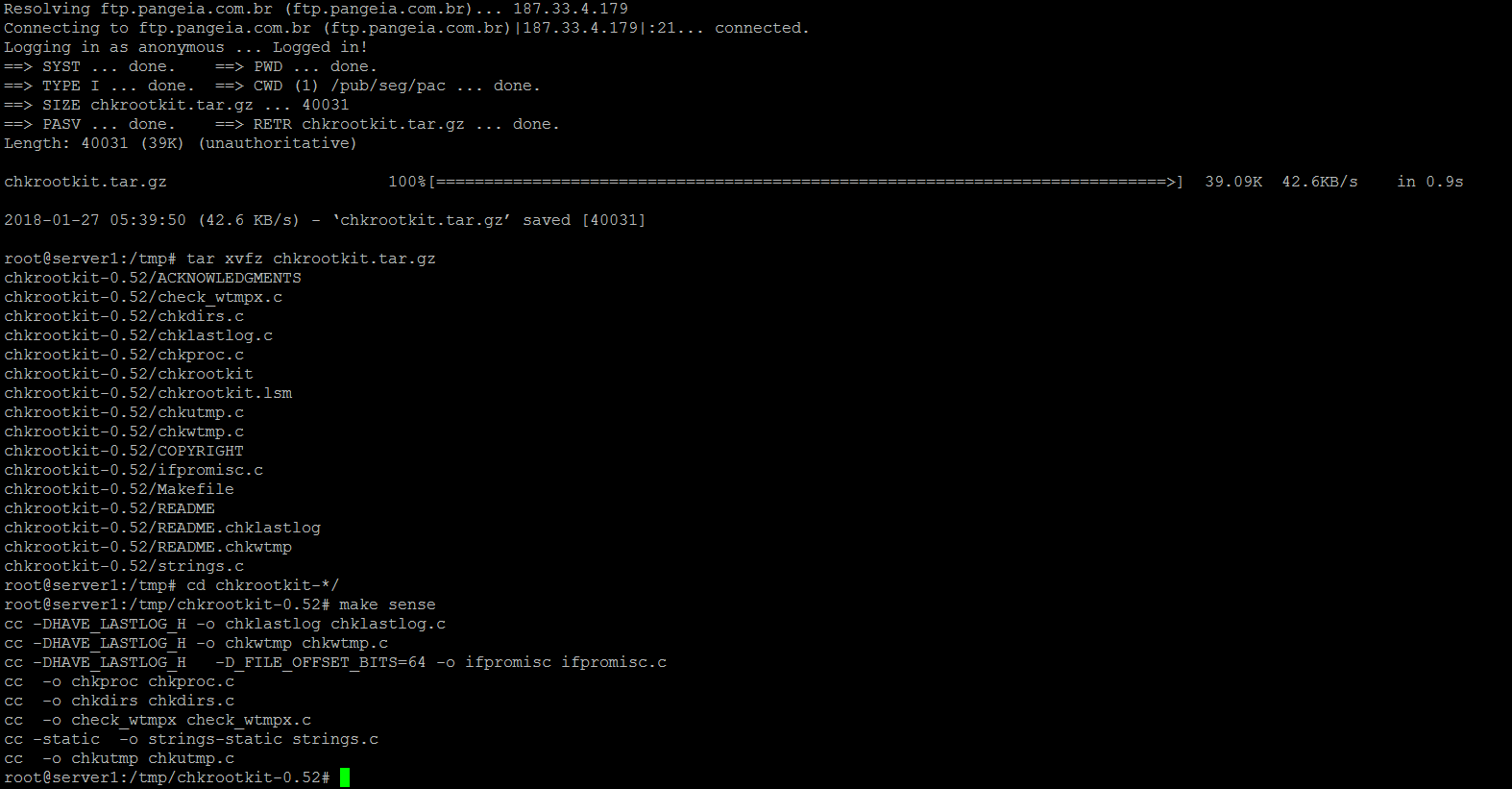
Run it by typing. Do you already have an account? You can also use Chkrootkit, Rkhunter, and ISPProtect to scan a system if you have suspicious activities such as high load, suspicious processes or if the server suddenly starts sending malware. No, create an account now.

Very helpful and useful article. If your system is exposed directly to the internet you will notice that there are lots of malicious activities in the internet, and you will get a feeling why security is very important.
ISPProtect contains 5 scanning engines:.
If a worm, rootkit, etc. Do you already have an account? Just a little info: Thanks for mentioning unhide. In order to start portsentry at boot time do the following: This may be an attempt to spoof the checker.
You can easily check this using lsattr and look for s - i -a attributes in tools like ps, find etc. While a firewall and regular system updates are a good first defense to keep the system secure, you should also regularly check that no attacker came in. This document describes how to install chkrootkit and portsentry. You can even run chkrootkit by a cron job and get the results emailed to you.
This is normal and nothing to worry about.
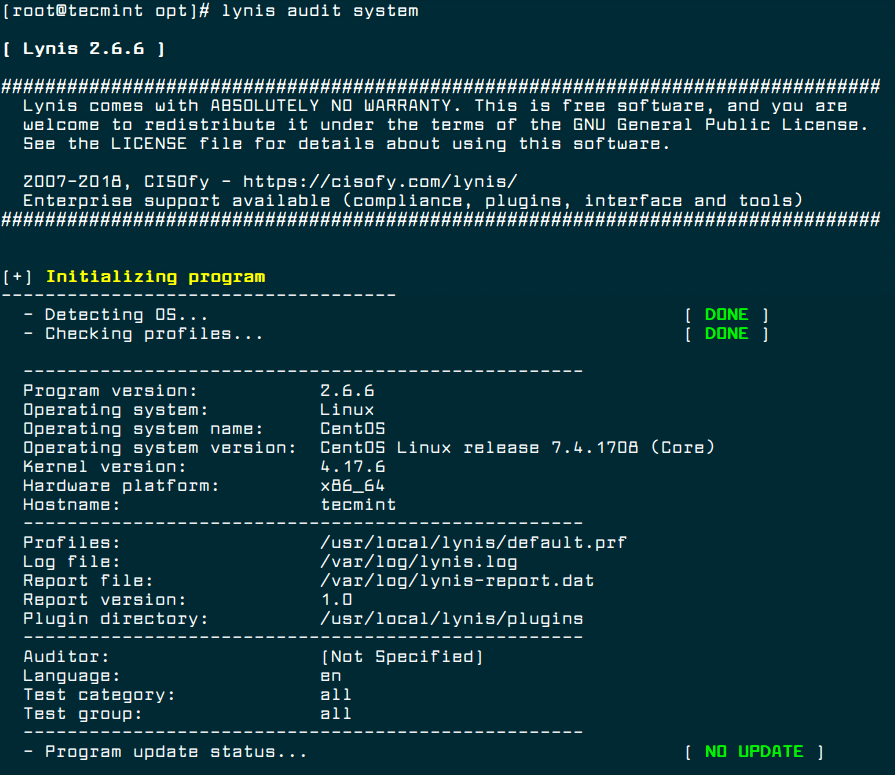
Original location of this document: The names of the infected files are shown on the screen at the end of the scan and the results are stored in file in the ISPProtect install directory for later use:.

No comments:
Post a Comment